If you’ve ever been a tourist in London, then you’ve probably been to the Tower of London and viewed Britain’s most prized possessions, the Crown Jewels. For over 600 years, these golden crowns, orbs, scepters and other priceless objects have been protected in the Tower, available for public viewing and occasionally removed for ceremony under heavy guard. There have been several notable attempts to steal the Crown Jewels over the centuries, but incredibly none have been successful. This is much to the credit of the Tower Guards—officially known as Yeoman Warders—and the security policies and procedures they created and follow to a “T”.
As a security professional, I appreciate this impressive feat and am always looking for approaches to security I can re-purpose to help my clients protect their most prized possessions, specifically their data assets. In this short article, I walk through some of the security practices that have effectively safeguarded the Crown Jewels for centuries, assess how modern information security compares, and explore lessons that we can apply to safeguard our organizations’ digital “crown jewels”.
What Are Your Company’s Crown Jewels?
This is an easy question at the Tower’s Jewel House, as all 140 of the rings, swords, trumpets and other ceremonial items are cataloged. Many are even committed to memory by the Yeomen Warders who often recite them during visitor tours. This is where security begins because you can’t protect what you don’t know.
One of the first things I do when helping a client address their security issues is gain a firm understanding of their data assets — the digital information that is crucial to their mission, operations and even survival. Think about your organization’s most sensitive data assets. Do you know what they are? If you took five minutes to jot down everything that comes to mind, you could probably list a dozen data assets. Now imagine asking a few of your colleagues to do the same. What are the chances everyone would list the same data assets as being important to the organization? If you’re feeling a little doubtful, you’re not alone. The fact is, many organizations don’t have a firm grasp on what their data assets are, much less a common understanding among employees.

Identifying and categorizing your data assets are essential first steps to getting a handle on them and applying the appropriate level of security for their importance and sensitivity. Identifying the assets can be accomplished in many ways but a data-centric risk analysis is an effective method of focusing on data that are core to the success of the business. Common classification labels used to designate data asset sensitivity in business include: highly confidential, confidential, internal, and public. Government agencies often use: top secret, secret, confidential, and sensitive labels. Some organizations create variant classifications that suit their business needs. Whatever classification categories are employed, the important thing is to ensure categories are commonly understood by employees and applied consistently throughout the organization. It’s also important to remember that most security audits will start with the auditor reviewing the organization’s data and component inventory. If this doesn’t exist or is not reasonably up to date, the audit probably won’t get off to a good start.
Where Are They Stored?
If a particular item from the Crown Jewels collection is needed for a ceremony or cleaning, the Yeoman Warders know exactly where to find it. The Crown Jewels reside in the Jewel House, each specifically labeled and meticulously placed in a designated display case. Unfortunately, it’s not as easy for us to locate data assets in the same way the Tower Guards locate various jewels.
“4 out of 5 organizations don’t know where their sensitive data are located" [1]
When I speak with CIOs and CISOs, this often comes up as one of those things that keeps them up at night. The ease of data replication and transfer makes knowing where all data assets reside a particularly challenging problem. Often, the business side of an organization thinks the IT department knows where data assets are stored, while the IT team thinks the business owners know (or should know). Even organizations that understand what their data assets are struggle to articulate with confidence everywhere that data lives. Structured data in databases are relatively easy to locate, but unstructured data (e.g., in emails, spreadsheets, PowerPoint presentations) are much harder to track. Compound that with the use of externally accessible networks, cloud storage, and personal devices (i.e., bring your own device, or BYOD, practices) and the problem can become mind-boggling.
Who Has Access?
On occasion, extremely well-vetted Crown Jewel “custodians” remove ceremonial items from their secure and tightly controlled locations. Unsurprisingly, only authorized individuals within the Royal House are permitted to handle the Crown Jewels. Certain items, such as St Edward’s Crown, can only be touched by the Queen, the Archbishop of Canterbury, and the crown jeweler[2]. Access to other items is dictated by slightly more relaxed policies, but even then only a select few individuals with a legitimate need to access the jewels are permitted to do so.

Information security access control policies are important and should follow a “need to know” principle (sometimes also called “least privilege”) akin to practices upheld when protecting the Crown Jewels. This means that individuals should only have access to the data they need to perform their job functions. For example, a CEO may need access to sensitive financial information, but she probably doesn’t need access to the organization’s secret sauce recipe—its intellectual property—in order to run the company.

Access and authorization should be set by determining the minimal level of privileges required for a person to fulfill his or her duties. Unfortunately, privileged accounts are often handed out more liberally in practice and are rarely reviewed or decommissioned when the user’s role or responsibilities change.
Learning from the Past
We can learn a lot from security controls dating back to the medieval times. These approaches to security have proven effective at protecting the Crown Jewels and are applicable to protecting data assets in modern times. Below is a summary of the steps you can follow to protect your digital crown jewels.
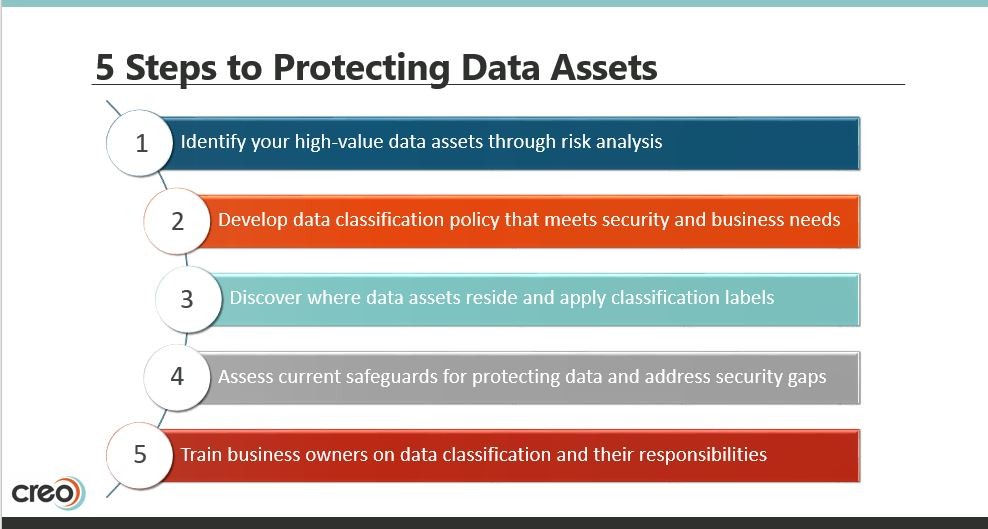
However, while there are lessons to be learned from the work of the Tower Guards, the comparison to protecting data assets today is not exactly apples to apples. Implementing security controls for data assets is exponentially more challenging than protecting 140 precious items in the Tower of London. Indeed, CIOs, CISOs and Compliance Officers have been given a very tall order in that regard.
If your high-value data assets are “everywhere”, you should know you’re not alone. But that doesn’t excuse complacency. It will take some elbow grease to get your data under control, as there is no quick and easy solution to this problem. There are tools that can help you wade through vast quantities of data, but truly getting a handle on data governance—knowing what your company’s crown jewels are, where they’re stored, and who has access to them—starts with following the above steps.
Don’t Put It Off
A lack of data governance is a problem that you may prefer to put off, but that’s really not a wise choice. In just five years, the data residing in your organization could be 60% greater than it is today. By 2025, the International Data Corporation (IDC) says worldwide data will grow 61% to 175 zettabytes. These ever-increasing quantities of data make it critical to address this problem sooner rather than later.
It’s never too early to get a handle on your data assets. Establishing data governance provides a framework allowing new data assets collected or generated to be appropriately classified, secured, and retained throughout the data’s life-cycle. Your organization’s crown jewels are important, so make it a priority to protect them.
CREO, Inc. helps organizations develop data governance programs for managing and protecting their high-value assets. Rett Summerville is the Cybersecurity & Compliance practice lead at CREO with over 17 years of information risk and security experience in software development, fintech, and consulting services. He is passionate about helping organizations transform their culture to improve security awareness, gain efficiencies, and maintain compliance. Rett promotes business-driven security and believes that good IT security practices can help companies be more competitive by enabling them to make better decisions quickly and confidently. Rett’s areas of expertise include integrated risk management, data security, regulatory compliance (GDPR, HIPAA, PCI DSS, CCPA) and security frameworks (NIST Cybersecurity, 800-53/171, ISO 27001/2, and CIS). Rett enjoys community service and is a volunteer high school pole vault coach. #creoculture #securityadvantaged #justdogreatwork

