As we close out the cybersecurity month of October, it’s a good time to think about what we can do better to protect ourselves in cyberland. The oldest security control of the internet is the password which has also been the biggest security vulnerability. Like many of you, I’m not a fan of passwords and have welcomed the migration to better authentication methods over the past few years. Multi-factor authentication, or MFA, and single sign-on are now used by over 57% of organizations, an increase of 12% year over year[1]. Nevertheless, most small businesses and the vast majority of consumer websites still rely on passwords for authentication, so it’s safe to assume that passwords aren’t going away anytime soon. As a security professional, passwords are still an important topic of conversation I have with my clients and a security control we continue to strive to improve.
The Password (People) Problem
If you have online accounts, you have probably been asked to update your password in the last year. If you’ve created a new account recently you most certainly have been told your first password choice “doesn’t meet our password policy” (usually 8 characters, upper + lower + number + special character). Why are websites suddenly forcing this level of password rigor?

Well, it’s because people tend to be very bad at choosing good or “strong” passwords to protect their online accounts. Here’s an actual list of the 30 most commonly used passwords on the internet in 2020. [2]
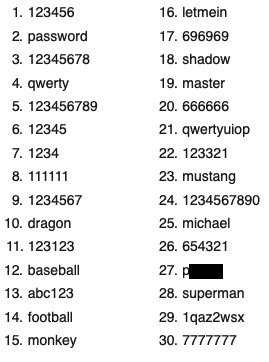
The source list I reference actually contains the top 100 most common passwords but those in the 25-100 range are a bit too racy for this article. This list says a lot about the password weakness problem we face and maybe more about the human psyche (another topic and outside my expertise).
Getting back to our password challenge, creating a complex password that you can remember, without writing down, is not so easy. You can easily spend 5 minutes crafting such a complex password. For example purposes, let’s say you come up with $ky2Moon. That’s a clever password meeting all the requirements and it’s somewhat memorable.
If you chose a password like this you should rightfully be proud of yourself for creating a “strong” password relative to most people. But, regardless of what the password strength meter might tell you, mathematically speaking this is not a strong password. I’ll explain why later.
Password Reuse
Since our clever password took some time and creativity, it’s understandable you would want to re-use it at more than one website. After all, how many clever passwords like this can the average person remember? We tend to use our favorite password at many of our most important websites. The average person reuses each password 14 times. [3] It only takes that clever password to be compromised one time and a cyber-criminal could have the keys to your kingdom, which may extend into your professional accounts.

“73% of users duplicate their passwords in both their personal and work accounts” [4]
Unfortunately, websites that store our passwords sometimes get hacked and the user info is sold on the dark web. The website https://haveibeenpwned.com is a repository of hacked user accounts and contains over 500 million user ID and passwords to-date. If your favorite sites are hacked, your clever password may end up exposed to many.
What makes a Password Strong?
A password’s strength is directly correlated with its entropy.

Entropy is a measure of randomness or disorder often used in statistical mechanics. A password with high entropy is difficult to crack through brute force attack, even using a supercomputer. For example, a 10-digit numeric password has very low entropy of 33 bits which a laptop can crack in a blink of an eye (0.0004 seconds). Our password, $ky2Moon has 52 bits of entropy and a laptop can guess this in 3 minutes of processing (0.02 seconds for a supercomputer). Password strength increases exponentially with bits of entropy, so an additional 1 bit of entropy increases the time it takes to crack the password by a power of 10.
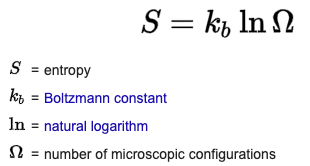
Entropy occurs everywhere in nature and affects many aspects of our daily lives. The sequence of corn kernels popping in the microwave has very high entropy and would take hundreds of millions of years for a supercomputer to predict. For curious readers, entropy is calculated as follows and you can access an online entropy calculator here:
The Next Generation: Passphrase
Earlier this year, the FBI published the recommendation to use passphrases instead of passwords.[5] The FBI’s guidance is to use a combination of words instead of a complex password you’re likely to forget or have to write down. For example, the passphrase:
brown cows drink chocolate milk
is actually a strong password. It’s okay if it doesn’t make sense – in fact, it’s better if it doesn’t. You can get creative. Passphrases offer several benefits over passwords.
Memorable
First, they can be easier to remember. When learning the strings on the guitar (E A D G B E), beginners often are taught a mnemonic such as Eddie Ate Dynamite, Good Bye Eddie. Mnemonic phrases are useful because they are easy to remember.
Simple
Second, passphrases don’t need to include the combination of special characters and upper/lower case to be effective. It’s perfectly acceptable for passphrases to be entirely lower case without special characters, unless you prefer to include them.
Strong
Third, passphrases have high entropy. The above passphrase has 117 bits of entropy which even a supercomputer could not defeat within 37 billion years of processing. This might be hard to believe, but it’s true.
Preventing Passphrase Reuse
Passphrases are a big improvement over passwords but they can become ineffective if you reuse the same phrase at multiple sites. How do you create and remember unique passphrases for each site? Use your creativity.

What jumps out to you about the site? Is it a color, word, purpose, character? Try to incorporate that into your passphrase. For example, if I’m at my bank site I might tailor my passphrase to:
brown cows eat chocolate money
There are no rules other than to avoid common phrases, i.e., mary had a little lamb. It’s best to get creative, just make sure it is memorable to you.
Password Managers
Not all websites allow passphrases today but that will change in time. The National Institute of Standards and Technology (NIST) has published guidelines for developers to allow up to 64 character password fields to support passphrases. [6] But until web developers implement the new guidance, consider using a password manager. This is a fairly secure option for keeping your passwords locked in an electronic vault. Password managers allow you to use a passphrase to keep your password vault protected. Some will also warn you if you’re using a weak password, or the same password at multiple sites. Some examples of commonly available password managers include: Lastpass, KeePass, 1Password, Dashlane.
Password managers are not a perfect solution to the password problem and they have their own security risks but they are effective at eliminating the need to remember complex passwords and they also help you avoid password reuse.
Conclusion
It’s cybersecurity month so even if your favorite websites don’t allow you to start using passphrases and you’re not ready for a password manager, now is still a good time to update your traditional passwords, especially if you haven’t changed them in a while, it’s on the common passwords list or you find it in https://haveibeenpwned.com. Take a moment to improve your password approach and keep your online accounts safe.
CREO, Inc. helps organizations deploy strong authentication and security solutions to protect high-value systems and data assets. CREO is recognized in the 2020 Inc 5000 list of fastest growing companies in the US.
Rett Summerville is the Cybersecurity & Compliance practice lead at CREO, an innovative management consulting firm that shapes growth companies into healthy successful organizations. Rett is a seasoned IT security and risk management leader with over 17 years of experience working in technical and business roles in software, fintech, and consulting services. He is passionate about helping clients transform their culture to improve security awareness, gain efficiencies, and maintain compliance. Rett promotes business-driven security and believes that good IT security practices can help companies be more competitive by enabling them to make better decisions quickly and confidently. Rett’s areas of expertise include integrated risk management, data security, regulatory compliance (GDPR, HIPAA, PCI DSS, CMMC) and security frameworks (NIST Cybersecurity Framework, 800-53/171, ISO 27001, and CIS). Rett enjoys community service and is a volunteer high school pole vault coach.
#inc5000 #creoculture #securityadvantaged #justdogreatwork
Sources:
- https://www.techrepublic.com/article/more-companies-use-multi-factor-authentication-but-security-still-weak-from-poor-password-habits
- https://en.wikipedia.org/wiki/Wikipedia:10,000_most_common_passwords
- https://www.darkreading.com/informationweek-home/password-reuse-abounds-new-survey-shows/d/d-id/1331689
- https://www.microsoft.com/security/blog/2019/08/20/one-simple-action-you-can-take-to-prevent-99-9-percent-of-account-attacks/
- https://www.fbi.gov/contact-us/field-offices/portland/news/press-releases/oregon-fbi-tech-tuesday-building-a-digital-defense-with-passwords
- https://pages.nist.gov/800-63-3/sp800-63b.html
- http://passwordstrengthcalculator.com/index.php

